Yesterday (June 27th, 2017) a worldwide, massive attack hit different IT infrastructure with a so-called ransomware the whole day. At the moment it is not known who and what is affected. It was only noted that the well-known US pharmaceutical company Merck, Beiersdorf but also computers of the wrecked nuclear plant Tschernobyl were attacked.
CIPHRON wants to show you the the most important information such that you are able to understand how the attackers proceeded.
The attack onto the systems exposed to the internet was, after all what is known, possible through the vulnerability EternalBlue which is known from the WannaCry ransomware. WannaCry is a ransomware which got attention through news media six weeks ago because critical infrastructure like the british National Health Service (NHS) was hit worldwide. A ransomware is a malicious software which encrypts data on afflicted systems and blackmails the affected persons or institutions to pay a ransom. The ransom has to be paid in Bitcoin in most cases.
It is characteristic for the most ransomware attacks that they are fully automatized.
EternalBlue is a vulnerability which uses a coding failure in Microsoft's implementation of the file transfer protocol SMBv1 and provides access to internal networks throug it. The exploit which utilizes the vulnerability uses a so-called buffer overflow: Buffer overflows are a vulnerability class which describes that a given memory section is written beyong the section's borders. This allows the ransomware to write a malicious program, the so-called payload, into the memory and to execute that certain program. In EternalBlue's case the vulnerability was a faulty comparison between two different variables of different size inside the SMBv1-code. A "word" variable has a size of 2 bytes while a "dword" variable has a size of 4 bytes. The vulnerable code compares such a word with a dword and allows the buffer overflow through it.
The bug was patched by Microsoft with the update MS17-010 on March 14th, 2017, already. If you have not installed that update we encourage you to do that urgently.
The current attack is delivered by the Petya ransomware. Petya was noted by specialist media last year. It has the same aim like WannaCry, the payment of a ransom, and uses the EternalBlue vulnerability in the current version.
If Petya got access to the internal network it uses the programs PSEXEC and Windows Management Instrumentation Command-Line (WMCI) to move lateral inside the network. By doing that it can attack much more computers. WMCI is an interface of Microsoft to allow remote maintenance and control of clients. Thus, the WMCI provides various options.
Petya attacks the victims perfidous: The ransomware does not encrypt the data for the first moment but utilizes the NTFS Master File Table (NTFS MFT). While it is possible to boot an operating system after hit by ransomware like WannaCry this is not possible after an attack by Petya.
Instead it reboots the computer one hour after infection. The user is confronted with a message that the NTFS file system must be repaired. In reality, Petya encrypts the data while the user sees the message.
This is an advantage for the user, however: If the user sees the certain message, he should shutdown the computer. It is possible to rescue the data and to copy it to a new device with specialized software.
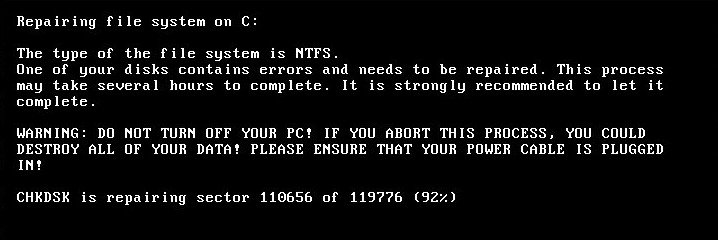
Monitor after reboot of the computer
. evade the attack we recommend the following steps if you have not already done them:
- Install the Microsoft update MS17-010 on all systems
- Create a rule in your firewall for port 445 such that only trusted IPs can use it
- Deactivate WMCI on your clients if not needed
- Create regular backups of your data
If you are affected do NOT pay the ransom - the e-mail account of the responsible criminals is already closed. This is the (german) statement of Posteo:
https://posteo.de/blog/info-zur-ransomware-petrwra..
We can only encourage you at this point that this attack shows again that you need a functional patch management and external audits. It is foolhardy to claim that the attack would be fully prevented by this measures - however, the created damage would be less for sure.
If you have questions about the article or information security in general, do not hesitate to contact CIPHRON.
-
-
CIWATCH
IT-Monitoring
Das umfassendste KnowHow zur Überwachung Ihrer IT-Services
Mehr erfahren
-
-
CIDESK
OTOBO
Geschäftsprozesse und Kommunikation perfekt managen
Mehr erfahren
-
-
CISQUAD
Wir machen sauber
Cyber-Angriffe abwehren und
Sicherheit wieder herstellen
Mehr erfahren
-
-
CICHECK
Wir hacken Sie!
Stellen Sie Ihre Sicherheit
auf die Probe
Mehr erfahren



